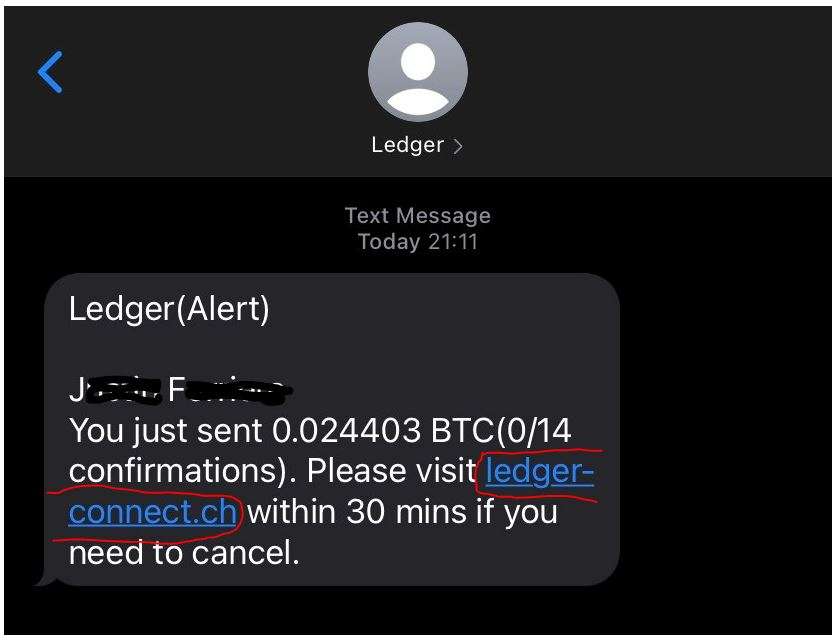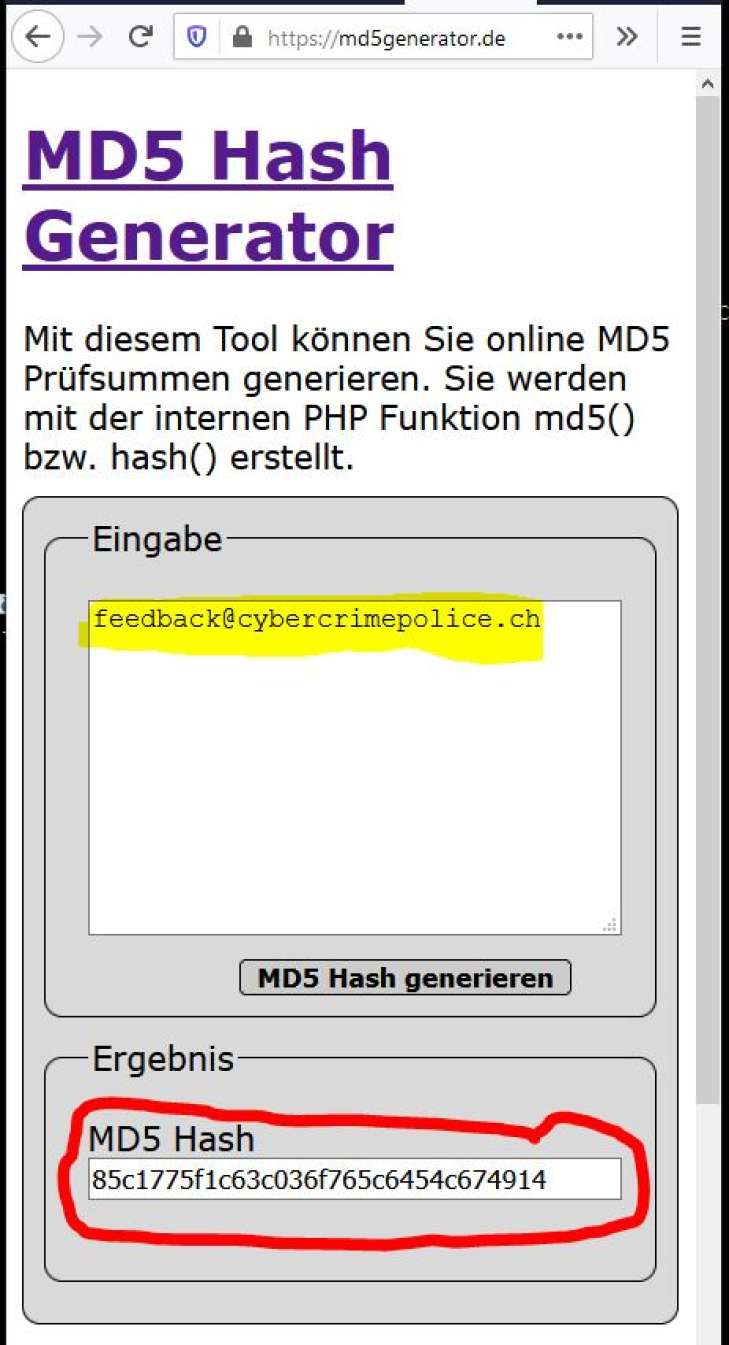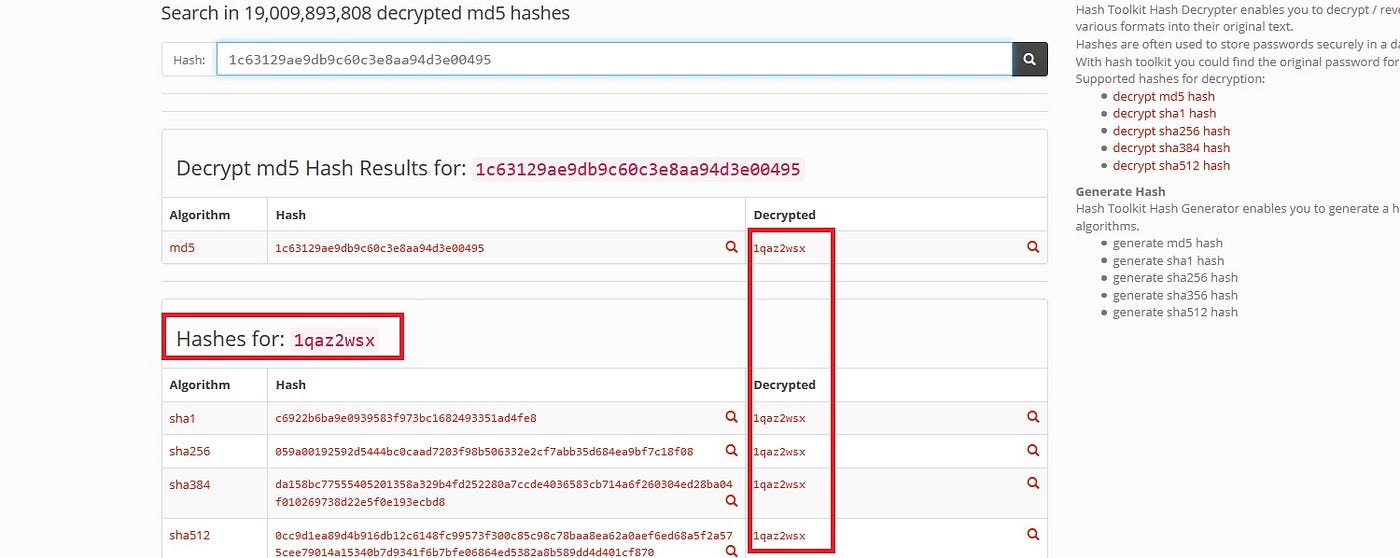
Symmetry | Free Full-Text | Fingerprint-Based Data Deduplication Using a Mathematical Bounded Linear Hash Function | HTML

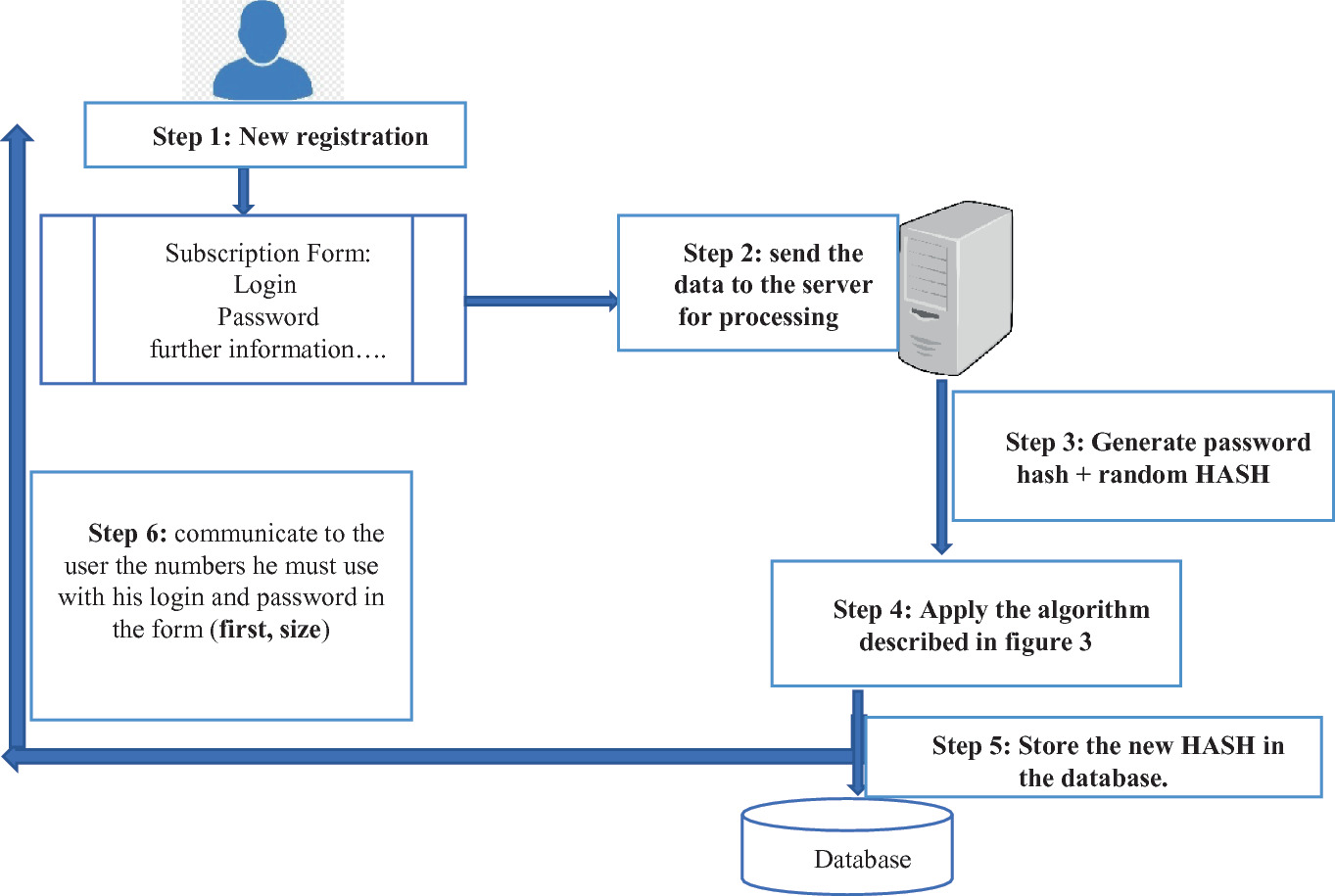
Solution Research and Application of E-Commerce and Network Information Security Based on Cryptography | Scientific.Net

Oracle OCI Data Transfer Service – A journey from Kestenholz/Jurasüdfuss/ Switzerland to Frankfurt and back – martinberger.com

Oracle OCI Data Transfer Service – A journey from Kestenholz/Jurasüdfuss/ Switzerland to Frankfurt and back – martinberger.com